When a company want to use guest wifi and to perform analytics on it, they have to take into account client devices like iOS are using mac randomization. iOS devices are doing this for a long time but Android devices started doing this now also.
Mac randomization is only visible when a client is not connected to a wireless network, the client device will present itself to the wireless network with a random mac address. Once the client connects to the SSID and authenticates it will show up with it’s real mac address.
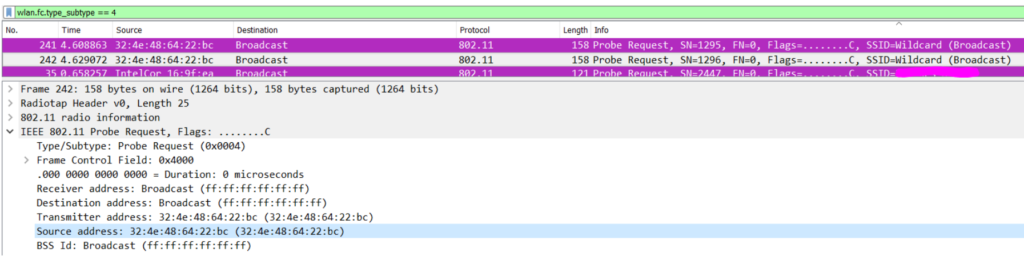
When you look at the capture you notice the mac address mentioned as the source address doesn’t match with the mac of your device. You can recognize the random mac address by looking at the 2 least significant bit of the octet, the are called local administered mac-addresses because the don’t match with any vendor OUI
Problem of mac randomization for company’s willing to perform guest counting have to take into account some platforms don’t count these local administered mac-addresses, so they don’t see the actual footfall or dwell time. On the other hand, some platforms do count the locally administered mac-address, if an iOS device is within range of the wireless network and sending probe request you will notice them. Because of the clients sending different mac addresses from the same device, you will see the same device multiple times on the same day. This will result in a footfall graph showing a lot more clients inside the building than in reality. You will still see a trend in the graphs from one week to another, if for instance a retailer is doing a marketing campaign and is seeing that the trend is going up compared to last week than he has a good idea that marketing did a good job
From a client perspective it is better to not remember all wireless networks on your phone if you don’t want to be tracked every time. Multi-site organisations, typically retailers or ISP hot-spots, use the same SSID for every location. Once you come close to the location with your phone and your phone has the profile of the SSID stored, it will try to connect. As soon as the phone is connected to the SSID, even when it is not authenticated on the captive portal it is showing it’s real mac address and it will be counted by the guest wifi analytics platform.

